Secured communication is inevitably a required norm in the world. To achieve the same, different methods are being approached. You must have heard the word "cryptography", which is really useful to safely transmit your signals by ensuring secrecy. Today, with advancements in this field, we have 2 of its widely known types i.e. private key cryptography (symmetric encryption) and public key cryptography (asymmetric encryption). What's the difference between them? Which one is better in what context? Let's see!
First, let's understand the basic terminologies:-
Cryptography:
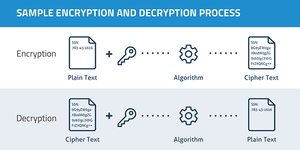
It is the technique of writing or storing information in a way that it’s revealed only to those who need to see it, and hides it from all others.
Encryption:
It is the implementation of cryptography. This converts data to ciphertext.
Decryption:
It is reverse of encryption. This converts ciphertext to readable data.
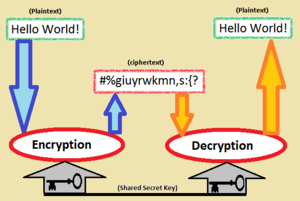
Symmetric Encryption:-
It is also known as private key encryption or private key cryptography. Here, only one key (secret key) is used for both encryption and decryption, by all the parties involved in communication over a network. That's why it is faster than asymmetric encryption.
The same key is kept for the entire session of communication. Therefore, this key is also known as "session key". This session key is either developed by both the parties (client and server) or alone by the client. If it is developed by the client only, then it is required to transmit to the server. In this case, a special concern is provided while transmitting this session key over a network. Because, if the key would get into the wrong hands, s/he can see all your transmitting information with any possible intention.
Modern approaches of symmetric encryption are executed using algorithms such as DES, QUAD, Blowfish, AES, 3DES, RC4 etc.
This type of encryption is used, when we are interested in transmission speed such as in transferring large files.
Asymmetric Encryption:-
It is also known as public key encryption or public key cryptography. Here, a pair of keys is used for encryption and decryption. These are the public key and the private key. The public key is used for encryption and the private key is used for decryption. Here, the private key is kept a secret to the owner and the public key is kept with all the servers to whom this client wants to connect.
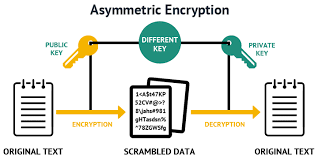
Understanding asymmetric encryption with workflow.
Suppose, a client wants to send a signal to a server. It will encrypt this signal using "server's public key" and will transmit over the network. When server will receive this signal, it will decrypt this, using "server's own private key".
The same is followed by a signal coming from the server. The server will encrypt the signal using "client's public key" and the client will decrypt this, using "client's own private key".
In this way, 2 keys equally participate in the process of public key cryptography. Due to the involvement of 2 keys, it is slower and more complex than symmetric encryption. Diffie-Hellman and RSA are the most widely used algorithms for asymmetric encryption.
Key differences between symmetric and asymmetric encryption:-
- Symmetric encryption involves only one key e.i session key. While asymmetric encryption uses two keys e.i public and private key.
- Symmetric encryption is faster and simpler than asymmetric encryption.
- Symmetric encryption is preferable over asymmetric encryption when a large file transfer is concerned.
- Asymmetric encryption is used to share the session key using which, symmetric encryption can be initiated.
- Asymmetric encryption is newer than symmetric encryption.
- In case of asymmetric encryption, no secret channel is necessary for the exchange of the public key.
With this, we have reached the end of this post. If you have any query regarding the topic, please let us know in the comments section below.
Have a good day!
